Proxy Servers Explained: Types, Use Cases, and How They Work
In today’s fast-evolving digital world, the term proxy servers often creates confusion. Many people use proxies without fully understanding how they work, and most online guides overcomplicate the topic.
This ultra-detailed guide aims to provide a complete understanding of proxy servers, including their working mechanism, types, protocols, authentication methods, benefits, trade-offs, common and advanced use cases, industry applications, security considerations, troubleshooting tips, and best practices. By the end of this guide, you will be equipped to leverage proxies for personal privacy, business efficiency, and automation tasks effectively.
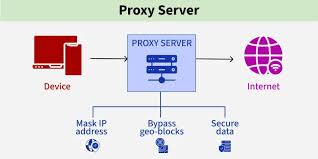
What Is a Proxy Server?
A proxy server is an intermediary between your device and the internet. When you request access to a website or online service, the proxy server handles the request on your behalf. The target website sees the proxy server’s IP address instead of your actual IP, providing anonymity and control.
Think of a proxy as a digital mask:
- It changes your IP address.
- Simulates a different geographic location.
- Allows you to manage how websites perceive your traffic.
Providers like ProxyWing offer reliable proxy layers, optimizing connection stability, reducing detection risks, and enabling advanced automation and browsing tasks.
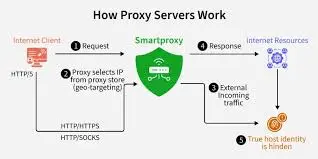
How Proxy Servers Work: Step-by-Step
The workflow of a proxy server can be summarized in these steps:
- Request Initiation: You type a URL in a browser or an app.
- Proxy Interception: The request is sent to the proxy server.
- Request Forwarding: The proxy forwards the request using its own IP address.
- Website Response: The website responds to the proxy, not seeing your real IP.
- Response Delivery: The proxy sends the data back to your device.
Example: Accessing a streaming service restricted in your country. The proxy server in the allowed region makes the request, allowing you access without being blocked.
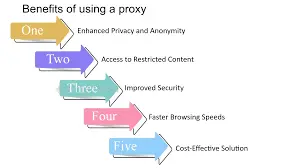
Benefits of Using a Proxy
Proxies provide several advantages for both individual users and businesses:
Privacy Protection
Proxies hide your real IP, making it difficult for trackers, ISPs, or hackers to monitor your online activity.
Geo-Location Flexibility
Access content restricted to specific regions, such as streaming platforms, ads, or localized websites.
Multiple Account Management
Maintain different IPs for each account, avoiding bans and detection on social media or e-commerce platforms.
Web Scraping Efficiency
Distribute requests across multiple IPs to scrape data continuously without being blocked.
Improved Network Performance
Some proxies optimize traffic and cache frequently accessed content, reducing latency.
Content Testing
Businesses can test websites and apps as users in different regions see them.
Security Enhancement
Proxies can filter requests, block malicious content, and provide an extra layer of security.
Limitations and Trade-Offs
Despite benefits, proxies have limitations:
- Speed Reduction: Additional routing may reduce connection speed.
- Website Detection: Some websites actively detect and block proxies.
- Reliability Dependence: Dependent on provider’s server quality.
- Wrong Proxy Type: Using the wrong type can result in errors, IP bans, or poor performance.
Types of Proxy Servers
Different proxies serve different purposes. Let’s examine them in depth.
Residential Proxies
Residential proxies use IPs from real households.
Advantages:
- Trusted by websites; less likely to be blocked.
- Ideal for location-specific tasks.
- Bypass CAPTCHAs effectively.
Disadvantages:
- Slower than datacenter proxies.
- Higher cost.
Use Cases:
- Social media management.
- Market research.
- Accessing geo-restricted content.
Case Study: A marketing firm used residential proxies to manage 500 social media accounts across multiple regions, avoiding bans and improving engagement metrics.
Datacenter Proxies
Datacenter proxies originate from servers rather than residential networks.
Advantages:
- Fast and affordable.
- Suitable for high-speed automation tasks.
Disadvantages:
- Easily detected by websites.
Use Cases:
- Bulk web scraping.
- Temporary sessions.
- Automation tasks.
Example: An e-commerce company used datacenter proxies to scrape competitor pricing every hour without exposing its servers.
ISP (Static Residential) Proxies
ISP proxies combine residential IPs with server stability.
Advantages:
- Stable for long-term sessions.
- Less chance of detection.
Disadvantages:
- Higher cost than datacenter proxies.
Use Cases:
- Account management.
- Prolonged automation tasks.
Example: A fintech startup used ISP proxies to monitor global stock data in real-time with consistent IP sessions.
Mobile Proxies
These proxies use 3G/4G/5G mobile networks.
Advantages:
- Hardest to block.
- Ideal for strict platforms.
Disadvantages:
- Expensive per IP.
Use Cases:
- High-volume automation.
- Testing mobile app performance across networks.
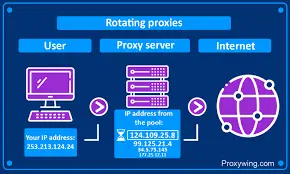
Rotating vs Static Proxies
- Rotating Proxies: Automatically change IPs; ideal for web scraping, testing, or automation.
- Static Proxies: Maintain a single IP for account stability and long sessions.
Comparison Table:
| Feature | Rotating Proxy | Static Proxy |
|---|---|---|
| IP Change | Automatic | Fixed |
| Best For | Scraping, Automation | Long-term accounts |
| Cost | Moderate | Higher |
| Detection Risk | Low | Moderate |
Proxy Protocols
HTTP/HTTPS
- Standard for web browsing and API requests.
- HTTPS encrypts data, enhancing security.
SOCKS5
- Highly versatile; works with scripts, apps, and automation tools.
- Supports TCP and UDP connections.
Proxy Authentication Methods
Username/Password Login
- Most common method; secure for both browsers and tools.
IP Whitelisting
- Grants access based on your device’s IP.
- Less flexible if your IP frequently changes.
Proxy vs VPN vs TOR
| Feature | Proxy | VPN | TOR |
|---|---|---|---|
| IP Masking | Yes | Yes | Yes |
| Encryption | Partial | Full | Full |
| Speed | Fast | Moderate | Slow |
| Use Case | Apps, Browsing | Full Device Security | Maximum Privacy |
| Cost | Low-Medium | Medium | Free |
Common Use Cases of Proxies
Web Scraping
Rotating proxies help collect large datasets without IP bans.
Multiple Account Management
Maintain multiple IPs for social media or e-commerce accounts.
Ad Verification
View ads as users in different regions to ensure correct display.
Market Research
Check competitor prices, stock, and trends without revealing your location.
Geo-Restriction Bypass
Access content or websites blocked in your country.
Privacy Protection
Hide your IP while browsing or using automation tools.
Streaming and Gaming
Access region-locked content or reduce latency in multiplayer gaming.
Advanced Proxy Strategies for Businesses
- IP Rotation: Avoid detection in scraping and automation.
- Location Targeting: Use proxies in specific regions for testing and marketing.
- Load Distribution: Spread requests across multiple proxies to avoid throttling.
- Security Layering: Combine proxies with firewalls and VPNs.
- Analytics and Monitoring: Track performance and detect blocks early.
Security Considerations
- Use only reputable providers.
- Avoid free/public proxies for sensitive data.
- Ensure encryption (HTTPS/SOCKS5).
- Monitor IP usage to prevent bans or blocks.
Troubleshooting Proxy Issues
- Slow Speeds: Switch servers or upgrade your plan.
- Blocked Access: Change proxy type or rotate IPs.
- Authentication Errors: Check username/password or IP whitelist.
- Compatibility Issues: Ensure proxy supports required protocol (HTTP, HTTPS, SOCKS5).
Industry Applications
- E-commerce: Competitor monitoring, account management.
- Digital Marketing: Ad verification, targeted campaigns.
- Finance: Secure access to market data.
- SaaS & Tech: Automation, API testing, software evaluation.
- Gaming & Streaming: Region-based access, reduced latency.
Case Study: A global marketing firm used rotating residential proxies to manage 10,000 client campaigns across multiple countries, increasing ad verification accuracy by 95%.
Best Practices for Proxy Use
- Select the right proxy type for the task.
- Ensure provider reliability and uptime.
- Use encrypted protocols for security.
- Rotate IPs for scraping and automation.
- Avoid free proxies for sensitive operations.
- Monitor usage and performance metrics regularly.
- Integrate proxies with VPNs for added security.
FAQs About Proxy Servers
Q1: Are proxies safe?
Yes, if using reputable paid providers. Free proxies may pose risks.
Q2: Can proxies improve speed?
Some optimize traffic, but generally, routing adds latency.
Q3: How do rotating proxies work?
They change IPs automatically, ideal for scraping or automation.
Q4: Proxy or VPN—which to choose?
Proxy for specific apps; VPN for full device security.
Q5: Can multiple proxies be used simultaneously?
Yes, with proper configuration, multiple proxies can handle different tasks.
Q6: Can proxies bypass strict security?
Proxies can bypass basic geo-blocks; strict security systems may still detect them.
For more
For more exclusive influencer stories, visit influencergonewild






4 Comments