Quantum Computing and Cybersecurity

Quantum Computing in Cybersecurity is poised to be one of the most transformative technological revolutions of the 21st century. Its ability to perform highly complex calculations at speeds far beyond the capabilities of classical computers is expected to reshape numerous industries from healthcare and finance to logistics, energy, and artificial intelligence. However, one area where quantum computing will have profound implications is cybersecurity. As the digital world becomes increasingly interconnected, understanding how quantum computing may reshape security, the potential threats it poses, and the strategies being developed to mitigate them is essential for organizations, governments, and individuals alike.
Understanding Quantum Computing

Quantum computing is based on the principles of quantum mechanics, the branch of physics that explains the behavior of matter and energy at microscopic scales. Unlike classical computers, which use bits (0 or 1) as the fundamental unit of information, quantum computers operate with qubits, which can exist in multiple states simultaneously due to a phenomenon called superposition. This allows quantum computers to process a vast amount of information in parallel, exponentially increasing computational efficiency for certain complex tasks.
Another key principle is entanglement, where the state of one qubit is directly correlated with the state of another, even across large distances. Any change in one qubit instantly affects its entangled partner, enabling sophisticated computations that are impractical for classical computers. These properties make quantum computers uniquely suited for tasks such as:
- Simulating molecular interactions in drug discovery and material science.
- Optimizing complex logistics networks in transportation and supply chain management.
- Enhancing artificial intelligence algorithms by processing enormous datasets more efficiently.
- Breaking traditional encryption algorithms that protect sensitive information in digital systems.
In short, quantum computers can solve problems that would take classical computers thousands, millions, or even billions of years.
The Cybersecurity Risks of Quantum Computing
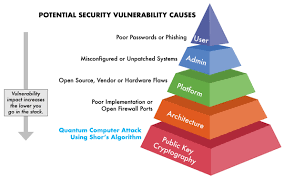
While quantum computing offers immense potential, it also introduces unprecedented cybersecurity challenges. Current digital security heavily relies on cryptographic systems such as RSA, Elliptic Curve Cryptography (ECC), and other asymmetric algorithms. These systems depend on the computational difficulty of factoring large numbers or solving discrete logarithm problems tasks that classical computers require years or centuries to solve.
Quantum computers threaten this balance. Using Shor’s algorithm, a sufficiently advanced quantum computer could break RSA or ECC encryption in hours or even minutes. The implications are profound:
- Sensitive data exposure: Personal data, financial records, intellectual property, and government secrets could be at risk.
- Compromised communications: Encrypted messaging, emails, and confidential communications could be intercepted.
- Financial system vulnerabilities: Digital currencies, online banking, and blockchain systems could face severe threats.
In essence, quantum computing could render many of today’s cybersecurity measures obsolete.
Key Cybersecurity Threats
Breaking Public-Key Cryptography
Public-key encryption algorithms such as RSA and ECC form the backbone of secure communications, authentication, and digital signatures. Quantum computers can efficiently solve the mathematical problems that underpin these algorithms, allowing attackers to decrypt data, steal private keys, or impersonate trusted entities.
Data Harvesting Attacks
Adversaries could collect encrypted data today and store it, with the intention of decrypting it in the future once quantum computing power becomes sufficient. This strategy, known as “harvest now, decrypt later,” could expose sensitive information even before quantum computers are fully operational.
Supply Chain Exploits
Quantum-powered attacks could target software and hardware supply chains, compromising firmware updates, digital signatures, or cryptographic verification mechanisms. This could allow attackers to insert malicious code or manipulate systems undetected.
Blockchain and Financial Systems
Cryptocurrencies and decentralized finance platforms rely heavily on asymmetric cryptography. Quantum computing could disrupt these systems by breaking cryptographic safeguards, potentially compromising digital transactions and smart contracts.
IoT and Critical Infrastructure Threats
Internet of Things (IoT) devices, industrial control systems, and energy grids increasingly rely on cryptography for secure communication. Quantum-enabled attacks could compromise these devices, posing risks to public safety and national security.
Post-Quantum Cryptography (PQC): The New Defense

To mitigate these emerging threats, researchers are developing post-quantum cryptography (PQC)—cryptographic algorithms designed to remain secure against attacks from both classical and quantum computers. PQC algorithms are built to work on existing hardware, facilitating a smooth transition without requiring an overhaul of current infrastructure.
The National Institute of Standards and Technology (NIST) began standardizing post-quantum algorithms in 2016. After extensive evaluation, the first suite of quantum-resistant algorithms is expected to be finalized by 2024. These algorithms will form the backbone of encryption systems capable of withstanding quantum attacks.
Leading Post-Quantum Cryptography Algorithms

Lattice-Based Cryptography
Lattice-based cryptography uses complex geometric structures called lattices to create secure cryptographic systems. These algorithms are highly efficient and resistant to both classical and quantum attacks, making them ideal for encryption and digital signatures.
Hash-Based Cryptography
Hash-based cryptography relies on the one-way nature of cryptographic hash functions. It is particularly suitable for digital signatures and authentication, offering robust protection against quantum-enabled attacks.
Code-Based Cryptography
Code-based algorithms leverage error-correcting codes to provide security. They are robust against both classical and quantum attacks, making them suitable for secure communication and long-term data storage.
Multivariate Quadratic Cryptography
This approach uses polynomial equations over finite fields, offering strong security against quantum-enabled adversaries. It is particularly useful for digital signatures and authentication systems.
Isogeny-Based Cryptography
A newer approach, isogeny-based cryptography, leverages the mathematical properties of elliptic curves. It provides compact keys and strong resistance against quantum attacks, though its practical adoption is still in early stages.
Quantum Key Distribution (QKD): A Quantum-Safe Solution

Beyond PQC, Quantum Key Distribution (QKD) offers an innovative method to secure communications using the principles of quantum mechanics. QKD allows two parties to generate and share cryptographic keys in a way that any eavesdropping attempt is immediately detectable, because measuring quantum states alters them.
Advantages of QKD
- Information-theoretic security: Unlike classical encryption, QKD security does not rely on computational difficulty.
- Instant intrusion detection: Any interception attempts disturb the quantum states, revealing the presence of an attacker.
- Future-proof: QKD can safeguard communications against both classical and quantum attacks.
Challenges of QKD
- Requires specialized hardware such as single photon detectors.
- Needs dedicated optical fibers or satellite links for communication.
- Scalability is limited, making it challenging to deploy across large networks.
- Cost-intensive implementation compared to software-based cryptography.
Despite these challenges, QKD complements PQC and represents a promising pathway for secure communication in the quantum era.
Preparing for the Quantum Threat Timeline

While fully capable quantum computers are not yet available, experts estimate that they could emerge within the next 10 to 20 years. Waiting until they arrive could leave critical data exposed to advanced attacks. To stay ahead of emerging threats, organizations must act now:
- Conduct risk assessments of sensitive data and cryptographic systems.
- Monitor advancements in quantum computing, PQC standards, and cybersecurity research.
- Invest in R&D to explore PQC algorithms and quantum-resistant solutions like QKD.
- Implement hybrid cryptography: Use both classical and post-quantum algorithms during the transition period.
- Collaborate with governments and standards bodies to align with initiatives such as NIST’s PQC standardization.
- Upgrade critical infrastructure: Secure financial systems, communication networks, cloud storage, and supply chains.
Implications Across Industries
Quantum computing will not affect cybersecurity in isolation it will have far-reaching impacts across various sectors:
- Healthcare
Protecting patient records, genomic data, and research information is crucial. Quantum-resistant encryption ensures sensitive medical data remains confidential. - Finance
Banks, investment firms, and fintech companies rely on encryption for transactions. PQC and QKD safeguard financial systems against quantum threats. - Government & Defense
Secure communications, intelligence, and classified information are vulnerable to quantum attacks. Post-quantum security measures are essential for national security. - Energy & Critical Infrastructure
Power grids, water systems, and transportation networks require quantum-resistant cybersecurity to prevent potentially catastrophic disruptions. - Technology & Cloud Services
Cloud providers must integrate PQC to secure customer data and maintain trust in digital services.
Building a Quantum-Resistant Future

Preparing for the quantum era requires a proactive and multi-layered approach
- Education & Awareness: Organizations must educate IT teams and executives about quantum risks.
- Policy & Governance: Develop policies for cryptographic upgrades and quantum-safe practices.
- Continuous Monitoring: Track advancements in quantum computing and cybersecurity standards.
- Collaboration: Partner with academia, industry leaders, and standardization bodies to share knowledge and best practices.
Adopting these measures ensures that organizations remain resilient as quantum technologies mature.
Conclusion
Quantum computing promises unprecedented computational power, but it also presents significant cybersecurity challenges. By embracing post-quantum cryptography, quantum key distribution, and proactive security strategies, organizations can protect sensitive data, maintain trust, and navigate the quantum future safely. Preparing today ensures that society can unlock the transformative potential of quantum computing while minimizing its risks, safeguarding digital assets, and securing critical infrastructures.
The quantum era is coming. The question is not whether quantum computing will disrupt cybersecurity, but how prepared we are to face it.
For more
For more exclusive influencer stories, visit influencergonewild